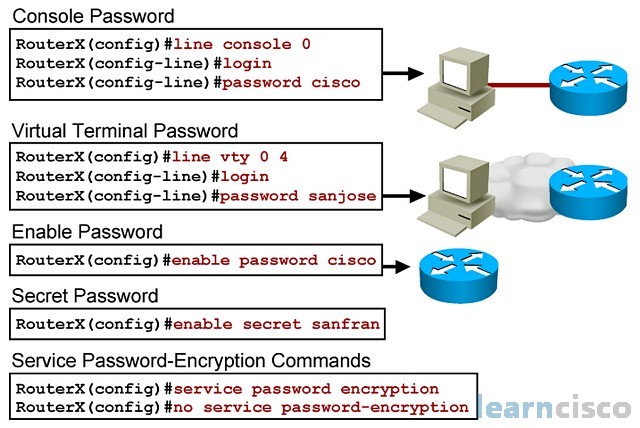
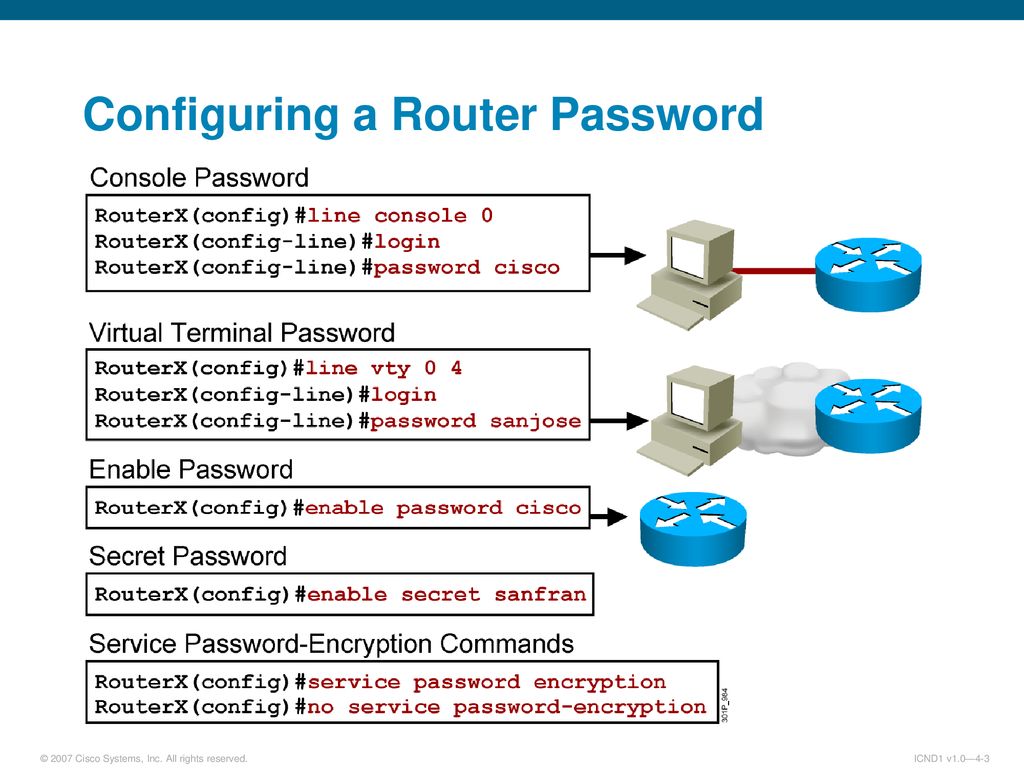
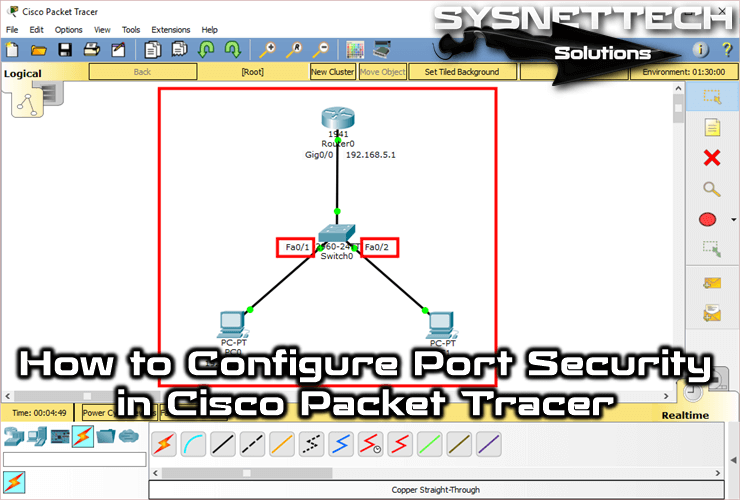
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press

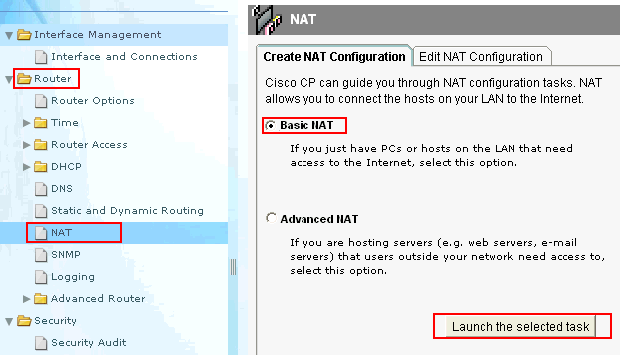
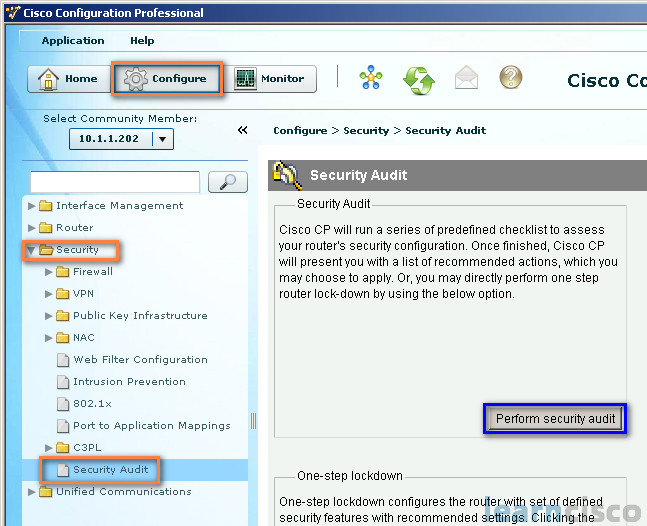
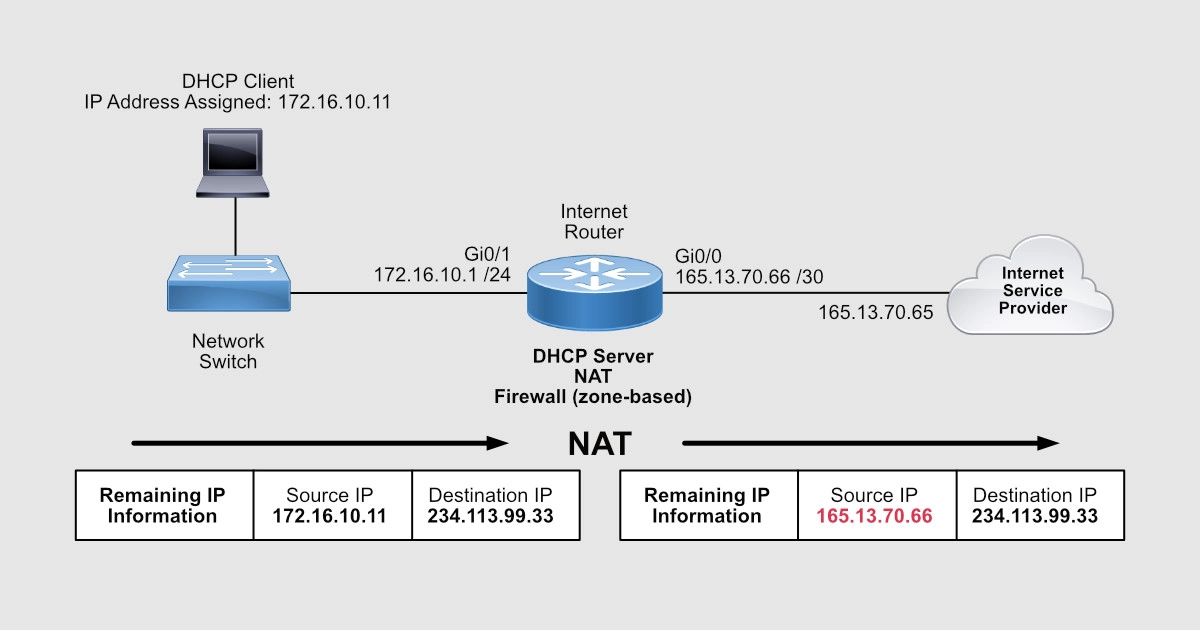
Learn to Configure the IOS Firewall on cisco router | Learn Linux CCNA CEH IPv6 Cyber-Security Online